Cloud Privacy: When the Extension’s Servers are Breached
It’s not enough to say your server in the Cloud is secure. When a company or organization says their data is secure, assume that’s on a spectrum, rather than an absolute stating of fact.
Just look at this Top 10 list from Digital Guardian of websites that have been hacked in 2015 (https://digitalguardian.com/blog/top-10-biggest-data-breaches-2015 ): from US government agencies, healthcare companies, and children’s toy manufacturers, to an anti-virus/personal data security company (oh how the irony gods must have loved that one). That’s just the big ones that got press, and that’s only for 2015.
Just as given the time, desire and resources, any safe can be broken into. So it goes with servers. Assume that any and all servers can eventually be breached.
Given that fairly reliable presumption, schools should not build a policy on if their data is secure in the cloud — it isn’t. Instead schools should ask of their providers what data is stored. The answer to that question will dictate the consequences of an almost inevitable data breach.
Extensions that are used in schools should not store data that is specific and personal in the cloud. They shouldn’t even process that sort of data in the cloud. Because if that data goes to the cloud, it is sitting on a server somewhere that is – like all servers – vulnerable to being breached.
So if the extension you’re using has to vacuum up and send to the cloud all that you view in your browser to read, or block adds, or summarize, or word predict, or whatever… (see the previous posts on this topic, (Cloud Privacy: How is your extension paying for its development?, Cloud Privacy: Can you turn your Extensions Off?, Extensions — What work is done in the Cloud vs. the local computer, Chrome extensions and Privacy — Questions to Ask) then that data is vulnerable and exposed. If it is being sent to servers in the US or other countries, it is subject to the surveillance and intelligence policies of that state, which might be quite different from Canada’s, too.
The point is, it doesn’t have to be like that. Developers chose to build extensions that function like that, if not for nefarious reasons, then simply because it’s cheaper and easier (again, see the previous posts listed above, for details).
Co:Writer and Snap&Read are the exceptions that prove the rule. Their writing (Co:Writer Universal ) and reading extensions (Snap&Read Universal ) send data to their servers in the cloud, yes. But it’s meta-data. It’s an analysis of the type of text the student is reading or they are writing — not the text itself or where it came from.
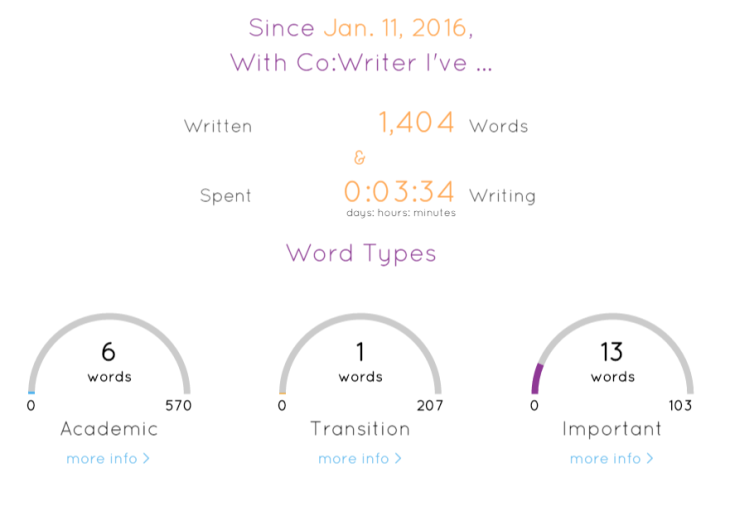
The reports tell us –depending which tool, Co:Writer or Snap&Read — the reading level of the text the student is reading, how many words they’ve read, what kind of important academic words are being used in their writing, how the group is doing — that sort of thing.
It doesn’t tell us things like:
- Which words they are.
- What text has actually been read.
- What sites have been visited and when
Don Johnston’s extensions won’t tell us that and can’t tell us that because that info is not sent to their server. If ever their servers are breached, the hacker would discover which kids are reading at a grade 6 reading level but not what they’ve read.
Think of the servers as a safety deposit box inside a bank. No bank is theft proof. But whereas the other safety deposit boxes might have various valuables that could be converted into cash, what would a thief find in the Co:Writer or Snap&Read box?
An inventory list, a summary of data and analysis of it. That’s it.
Nothing worth stealing.
The letter home when the data is breached
If (or when) your extension’s server is breached, according to Ontario law (I’m sorry but I just don’t have the wherewithal to confirm if this is the case in every province and territory. Please post comments and emails about the situation in your neck of the woods) the company/extension provider must (all the quotes here are from Privacy Breach Protocol Guidelines for Government Organizations, May 2014, by the Information and Privacy Commissioner of Ontario, Web site: http://www.ipc.on.ca)
…notify the institution promptly of any theft, loss or unauthorized use or disclosure of personal information… (pp. 19)
Once the company notifies the school board, the school board in turn must:
notify the individuals whose privacy was breached, by telephone or in writing
as part of “An incident management plan” that ensures,
..that legal, technical and organizational mechanisms are in place so that actual or suspected privacy breaches are reported and acted upon in a timely manner…
So, basically, the proverbial phone call or likely (since so many students have to be notified) note home.
If an app like Co:Writer or Snap&Read‘s servers are breached, that note home will be able to outline the metadata described above. No personal data could have been accessed by whoever hacked the servers because there is no personal data on the servers.
The note home from an extension that does gather that data because it sends all that information to the cloud to be processed, will have to detail that compromised information.
It is such a note home that has forced at least one school district in the US that I know of, to abandon an extension based reading/writing tool because of a server breach. Parents read the note and demanded that the subscription to the extensions be cancelled.
That district is now using Co:Writer and Snap&Read.
- Tags: cloud GAFE/ Chromebook Writing
- Bogdan Pospielovsky





Comments 0